Cyber Security Awareness Hub
Build Security Into Your IT Infrastructure & Keep Your Organization Safe
As technology is now a way of life our attack surface for hackers has grown. Given this, the threats of cyberattacks increase exponentially. Whether you are making purchases online, checking your email, responding to vendors or customers or using data in production, hackers are looming to get access to your data to hold you hostage with ransomware and take you and your business down.
A layered security approach combined with education is your best defense.
It’s no secret that cybercriminals’ tactics constantly become more advanced,
leaving everyone vulnerable if they don’t have the right training.

We have created a Cyber Security Awareness Kit, designed to be
delivered to your team in bitesize chunks.
We are sharing the resources and highlighting services your organization needs,
covering everything from multifactor authentication to software updates,
showing your users just how easy it is to improve their security posture.
We will be updating the resources and highlighting services your organization
needs each week covering everything from multifactor authentication to software updates,
showing your users just how easy it is to improve their security posture.
Featured Service of The Week:
MXINSPECT
Email Defense & Security Awareness Training
More than 90% of today’s cyber attacks target users through email.
While technology safeguards are important, they can’t stop everything.
That’s why you need educated employees as a strong last line of defense.
Quick Tip:
An effective security awareness training program shows your people how to avoid opening the door to a threat.
Protect your people from Today’s Email Theats
MXINSPECT Email Defense can protect organizations from email threats including phishing, malware, spam, and other forms of objectionable or dangerous content by leveraging the leading technologies in a suite designed for small business.
This cloud based enterprise-class Email Security, Continuity & Archiving product is designed specifically for SMEs and backed by MXINSPECT’s enterprise class security & infrastructure, the same technology that protects some of the largest and most security conscious companies in the world.
Email Protection
Information Protection
Email Archiving
Email Continuity
Advanced Threat Protection
MXINSPECT Security Awareness Training solutions engage your end users and arm them against real-world cyber attacks. Give your customers the ability to protect their people and organization from phishing, text and social attacks by up to 90% with our proven solutions.
Our Security Education Platform gives your customers the ability to identify risk, change behavior of end-users and reduce exposure to threats in their organization.
With our suite of security awareness training tools, your customers can integrate assessments, interactive training, reinforcement materials and comprehensive reporting features. Multinational organizations can deliver localized assessments and training in more than 35 languages.
Featured Service of The Week:
eCare Dark Web Monitoring
Credentials are Involved in More Than 60% of Data Breaches
Poor cyber hygiene could launch your data into Dark Web territory
Quick Tip: Establish training and other initiatives to help your employees learn and practice good cyber security hygiene. A single click by an untrained employee is all it takes for your data to end up on the dark web.
Train your team to be dark-web savvy.
Contact us to schedule a consultation
Our 24/7 Dark Web Monitoring solution provides critical alerts for business domain and employee credentials. The earlier you know about these compromises, the sooner you can reset passwords and resolve these security gaps.
We leverage the power of both advanced technology intelligence and human analysts to proactively search for and analyze compromises and exposed login credentials that can make your business a hot target for cybercriminals.
24 x 7 x 365 Monitoring
Identify and investigate exposed login credentials or pairs discovered directly linked to your business email domains or IP address details.
Alerts and Report Analytics
With 80,000+ domain compromises discovered daily, access reporting and analytics on industry trends and evolving risks and take preventative actions to avoid cyber threats.
Proactive Prevention
Cyberattacks are becoming increasingly inevitable. However, implementing Dark Web monitoring will help reduce the risks and threats caused by exposed employee credentials.
Overcome Password Reuse
Individuals often reuse the same login credentials accross multiple platforms, which makes them more vulnerable to credential theft. Overcome the risks related to bad passwords.
Contact us today to find out if your business is already exposed on the Dark Web.
Featured Service of The Week:
eCare Network Management
Software Updates are Important!
Outdated software often has vulnerabilities that allow malicious content through to you and your network.
Quick Tip: Run updates as soon as they become available & ONLY install updates from trusted sources

Our eCare services provide 24 x 7 monitoring and support for customer servers, workstations, firewalls and other equipment as well as services including Exchange and Active Directory.
Receive the highest level of support and problem resolution with eCare Premium. We will proactively monitor your network for issues, and our experts will always be on hand when you need them most.
Security
Monitoring
Performance
Expert Consulting
Our monitoring tools that are installed on your server, provide the close up snapshot of your network to ensure its health and stability.

Anti-Virus
Check

Security Patch Deployment

Logical Disk Space Check

Hardware & Software Asset Collection

Microsoft, Apple, & 3rd Party Patch Assessment
Your success is dependent on the performance and security of your business assets. Optimize and protect your IT investment with comprehensive IT security, support, implementation and maintenance from eMazzanti Technologies.
Build a strong cyber security culture with these helpful resources
Your most valuable asset is also your best defense: your people
To help you raise cyber security awareness among your users, we have curated a selection of free resources.
We invite you to use this kit to demonstrate just how easy it is to secure your business from cyber threats.
Receive Access to All Resources
Race to Embrace Multifactor Authentication (MFA)
Underline the importance of MFA. When you add layers of authentication, you add layers of security to your accounts, data, and systems.

60 seconds to better security:
What is Multifactor Authentication?

Attack Spotlight:
MFA Fatigue Attacks
Managing Passwords and PINs
Show users how strong passwords offer greater security with minimal effort.

The problem
with common passwords

Perfecting
Passwords
Phishing – Recognize, Report, Respond
Teach your users about the early warning signs of a phishing attack – and why fast reporting and response are crucial.

Phish Finder:
Spotting Warning Signs

Suspicious Emails:
Why Reporting is so Important
The Risks of Outdated Software
Show your users how outdated software exposes your organization to vulnerabilities, malicious payloads and data loss.

60 seconds to better security:
Why software updates are important
Infographic
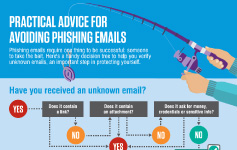
Practical Advice for Avoiding Phishing Emails
Phishing emails require one thing to be successful: For the recipient to take the bait. This “decision tree” is a helpful reminder that verifying unknown emails is an important step in protecting your data and devices.
Infographic

Recognizing and Avoiding
BEC Attacks
This infographic helps you understand what Business Email Compromise (BEC) is. If you believe you have been a victim of a BEC attack, alert your supervisor, financial institution, IT department, and authorities as soon as possible. Quick action can help to minimize the damage.
Infographic

Understanding
Ransomware
Ransomware is a type of malicious software — that is, malware — that blocks access to a device or data until a ransom is paid. Ransomware can affect computers and mobile devices, and both organizations and individuals could be targeted by attackers.Prevent an infection and be prepared to recover your data if you do get hit.
Infographic

The Facts about
Phishing
What would you do if a suspicious stranger came up to you on the street and tried to lure you down a dark alley? You’d probably sense danger and either walk away quickly or call for help. But what if the stranger approached you through email? You might feel it’s safe to click on a link in the email or open an attached file — but it’s a trap.
eBook

6 Known Wi-Fi Threat Categories Targeting Your Business and How to Defend Against
More and more devices are leveraging Wi-Fi connectivity. This trend isn’t expected to slow down anytime soon, and while your customers and employees demand access to fast Wi-Fi, you might not know the huge gap it’s leaving in your security.
eBook

Escape
the Ransomware
Maze
Ransomware is an ever-evolving form of malware designed to steal business-critical data and then sell it or encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption.
eBook

Unified Security for a Reconnecting World
When users are a network away, threats are closer than ever!
Providing remote access to corporate resources and data in a way that maintains the “on-site” user experience is critical to the continuity of your business – but doing so securely can be a daunting task. The stakes are high; one wrong click can bring your business grinding to a halt.
eBook

Protecting
the End User
Today’s attacks target people, not infrastructure. Organizations are spending more than ever on cyber security and getting less value from it. Attacks keep getting through. Sensitive information keeps falling into the wrong hands. And data breaches keep making headlines.
Workshop
Close Up The Security Blindspot With Detection and Response (EDR)
Gianluca Busco Arrè,
Vice President Global Endpoint,
WatchGuard Technologies
Workshop
Today’s
Threat Outlook
2022/2023
Corey Nachreiner,
Chief Security Officer,
WatchGuard Technologies
Workshop
Security Framework
and Compliance
For Your Business
Carl Mazzanti,
Co-Founder & President,
eMazzanti Technologies
Workshop
Never Pay Ransomware. Do You Really Want to be a Good Customer for Bad People?
Nirvan L. Ramoutar, Senior Business Development Manager,
eMazzanti Technologies
Workshop
Dark Web &
Security Awareness
Training
Peter Clarke,
Business Development Manager
eMazzanti Technologies
Workshop
Wi-Fi-6 Why Your Hybrid Workforce Needs Additional Security and Access Support
Nick Rittenhouse,
Senior Network Engineer
eMazzanti Technologies
Workshop
10 Easy Steps to
Protect Your Organization
in the New World
Jessica Brown,
S. Business Development Manager
eMazzanti Technologies
Staying safe online doesn't have to be difficult.
But with people at the heart of cyber attacks, user knowledge and awareness are key.
Receive Access to All Resources!
Quick Facts & Tips
More than 90% of today’s cyber attacks target users through email
While technology safeguards are important, they can’t stop everything. That’s why you need educated employees as a strong last line of defense.
Quick Tip:
An effective Security Awareness Training program shows your people how to avoid opening the door to a threat.
Credentials are Involved in More Than 60% of Data Breaches
Poor cyber hygiene could launch your data into Dark Web territory. A single click by an untrained employee is all it takes for your data to end up on the dark web.
Quick Tip:
Train your team to be dark-web savvy. Establish training and other initiatives to help your employees learn and practice good cyber security hygiene.
Software Updates are
Important!
Outdated software often has vulnerabilities that allow malicious content through to you and your network.
Quick Tip:
Automate Patching or run updates
as soon as they become available.
ONLY install updates from
trusted sources.
Build a more secure culture with these services!
eCare Network Management
Security, Performance, Monitoring and Expert Consulting
Our monitoring tools that are installed on your server, provide the close up snapshot of your network to ensure its health and stability.
– Anti-Virus Check
– Security Patch Deployment
– Hardware & Software Asset Collection
eCare Cloud Backup
UNLIMITED Backups & Data protection
for Microsoft 365
Many small businesses are not aware or prepared for the detrimental impacts that data loss can have on their operations.
eCare Cloud Backup can help mitigate these risks.
eCare SOC
Security Operations Center
24x7x365
Our great security service offerings include our ground-breaking Managed Detection and Response (MDR). Essentially, all SIEM solutions rely on the collection and analysis of logs. Our main advantage is in our 24/7 Security Operations Center (SOC).
Security Awareness Training
Change User Behavior
to Reduce Risk
With MXINSPECT Security Awareness, you get enterprise-level security awareness training. What’s more, it’s customized for your needs. It helps you reduce successful phishing attacks and malware infections. And it turns your users into a strong last line of defense!
Penetration Testing
Put Your Defenses
to the Test
The best way to know how intruders will actually approach your network is to simulate a real-world attack under controlled conditions. This allows us to pinpoint actual risks posed to your company from the perspective of a motivated attacker.
eCare Secure Route
Cloud-delivered network security and web filtering that protects any device, anywhere
When a user is off-network, they are more vulnerable and the organization lacks visibility and protection. If you rely on perimeter security alone, you’re not fully protected. These gaps open the door for malware, ransomware, and other attacks.
MXINSPECT Email Defense
Complete Defense Against
Today’s Email Threats
MXINSPECT can protect organizations from email threats including phishing, malware, spam, and other forms of objectionable or dangerous content by leveraging the leading technologies in a suite designed for small business.
Dark Web Monitoring
We go into the dark web
to keep you out of it
Digital credentials, such as usernames and passwords, connect you and your employees to critical business applications, as well as online services. Unfortunately, criminals know this — and that’s why digital credentials are among the most valuable assets found on the Dark Web.
Multi-Factor Authentication
Passwords are
no longer enough
MFA is a method of logon verification that adds a layer of security beyond just a simple username and password. It prevents unauthorized access that can result from lost or stolen passwords, while enabling verified users to easily access their accounts and information.
Free Offers
Preliminary Dark Web Scan

Are your credentials for sale on the dark web? We go into the dark web to keep you out of it.
Email Vulnerability Test

Protect your employees from domain spoofing attacks and increase email deliverability.
Keep your company’s most sensitive data safe with expert Cyber Security Services, consultation,
and crisis control from eMazzanti Technologies.
We expertly ensure all your security software is comprehensive and up to date, your emails protected, and your data encrypted—all while monitoring your network round the clock for suspicious activity.
We have the technology, people, and processes to deliver premium cyber security solutions
that are cost-effective and scale as your business evolves.

Start Protecting Your People Today
Cyber Security Articles
Insights to help you keep your business secure, in compliance, and thriving.
View all articles about Cyber Security
Let’s get started
Please contact our team or complete the form.
A representative will contact you shortly.
Let's Talk
We’ll chat about your business, how you use technology, and what you want to get out of IT.
Develop a Plan
You’ll choose the IT service agreement that works best for your organization.
Start Your IT Experience
Within days, you’ll be experiencing IT like never before.
T. 844-360-4400
[email protected]
Cyber Security Assessment

The time is NOW
to Confirm Your Cyber Strategy!
Preliminary Dark Web Scan

Are your credentials for sale on the dark web? We go into the dark web to keep you out of it.
Email Vulnerability Test

Protect your employees from domain spoofing attacks and increase email deliverability.










