We protect organizations against cyber threats through continuous monitoring.
We have the technology, people, and processes to deliver a premium cyber security monitoring solution
that is cost-effective and scales as your business evolves.
Threats are inevitable. Monitoring is everything!
Regardless of the size of the organization, if the business is connected to the internet, it is at risk of cyber-attack.
Here is what you need to know:

Cyber Security Requires Monitoring
Guaranteeing an organization’s safety includes detecting any malicious and unusual activity, which takes time, expertise, and the right technology.

Threats Can Occur Outside Office Hours
This is why it is essential to have dedicated security experts and systems that will be working 24x7x365 to monitor your business’s network.

Data Retention is Important
The retention of log data for certain regulated industries such as finance or healthcare is required. In addition, the stored data is key to further investigations.
Our security engineers triage and analyze alerts and then provide complete Incident Response guidance and remediate these events for your business. We don’t stop at just an automated discovery of cyber-threats!
- While we utilize several Security Information & Event Management (SIEM) technologies in the cloud, we go far beyond automated alerting. Our engineers provide “eyes on” analysis and complete Incident Response guidance to ensure that our customer’s security events are completely remediated before data, money or brand reputation is lost.
- While our services do help companies meet compliance regulations, both in monitoring and storage of logs, our primary service focus is security.
- Our service is designed to detect and remediate cyber-threats by performing real-time automated monitoring, supplemented 24x7x365 by human expert analysis of critical infrastructure device logs.
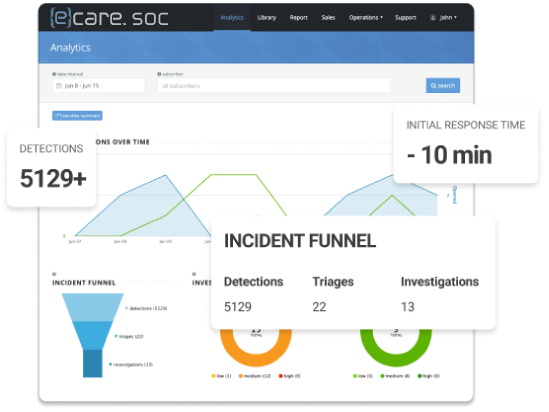
eCare SOC includes the human component required to triage, analyze and determine remediation for an event.
We completely mitigate the event for your business, step-by-step.
The threat is eliminated and your business is protected.
Why eCare SOC?
Fully managed Security Threat Monitoring as-a-service.
One Service includes ALL:
24/7 Security Operations Center. (SOC)-as-a-service
Incident Response Team (IRT) and Forensics IRT-as-a-service
Cloud based Security Information & Event Management (SIEM). (SIEM)-as-a-service
Monitoring Includes:
Threats On-premise
Cloud (AWS,Azure) or Hybrid Threat & Log Management (with storage)
24/7 Security Operations Center (SOC) Security Incident Response (IRT) & Forensics Office365 Security Monitoring Over 250 Products supported (e.g., Firewall, Domain Controllers)
Agent-less cloud-based SIEM Solution – one hour to on-board
Benefits:
One month opt-out. No penalty!
One low monthly subscription fee per device
One hour to implement Security Monitoring Solution
Office365 Security Monitoring
Over 250 products supported (e.g., Firewall, Domain controllers)
Agentless cloud based SIEM solution
10 minutes SLA response time
Business Security through 24/7
Cyber-threat
Monitoring and
Response
No company wants to experience a data breach but it happens all the time. While larger companies can often weather the financial and PR storms associated with a breach, the average small business closes their doors within 6 months of a cyber-security incident. What’s worse is that a vast majority of breaches are active within the network for months or years before detection – the only thing missing in these cases was a security expert looking for the evidence of a compromise.
Don’t allow your business to be a victim of a cyber-hack!
Let skilled security experts keep watch over the activity on your network. By applying cutting-edge SIEM (Security Information and Event Management) technology and established threat intelligence, suspicious activity and security incidents on your network can be identified and remediated as they occur.
Real-time Log Collection
As devices on your network generate logs and events, they are collected and transmitted to the cloud in real time for automated correlation.
Accurate Detection
Thousands of security correlation rules enable speedy evaluation of millions of network events to identify suspicious irregularities.
Human Expertise
Every security event identified by the cloud-based, 24×7 cyber-threat detection engine is viewed and evaluated by a trained cyber-security expert.
Threat Intelligence
Detailed analysis of valid security alerts are initiated within a state-of-the-art Security Operations Center (SOC) – staffed 24x7x365.
Security Response
Threat mitigation and remediation procedures using industry best practices are provided either remotely or on-site to ensure business continuity.
Status Reporting
Executive-level and in-depth technical reports provide a view of the number and type of threats your network is facing.
Our process combines cloud-based technology, highly-trained security experts and
a security response team who take action on any incidents targeting your network.
“Prevention Is Ideal, Detection Is Essential”
Protect your network from these threats and more:
Port scans, host scans, denied scans, sudden change of traffic between certain IPs or other anomalies in traffic.
Network server/device and admin logon anomalies – authentication failures at all times and unusual IPs.
Network access irregularities from VPN, wireless logons and domain controller.
Account lockouts, password scans and unusual logon failures.
Rogue endpoints, wireless access points.
Botnets, mail viruses, worms, DDOS and other “day zero” malware identified by cross-correlating DNS, DHCP, web proxy logs and flow traffic.
Abnormalities in web server and database access.
Cyber-threat monitoring and detection are the cornerstones of an effective IT security strategy. But collecting the right data, parsing and analyzing it into manageable and useful pieces of information is an extremely complex task.
Our 24×7 security service employs automated technology, paired with a staff of security experts, to reduce the risk and complexity of protecting your critical network systems.
Ransomware Detection
eMazzanti Technologies’ eCare SOC Services aid in the prevention of ransomware
While rare, it is possible that important files encrypted by ransomware may be decrypted or restored, however preventing the attack in the first place is ideal.
By actively monitoring a system’s logs, and by using the right technology and expertly trained analysts, the ideal can be proactively achieved. Thus, by detecting a ransomware attack, you will not only save an organization from paying the ransom, but you can also prevent system down time and the inevitable PR storm that could follow such an attack.

Managed Detection and Response (MDR) 24x7x365

Our great security service offerings include our ground-breaking Managed Detection and Response (MDR). Essentially, all SIEM solutions rely on the collection and analysis of logs. Our main advantage is in our 24/7 Security Operations Center (SOC).
Many MDRs are developed and operated solely to detect threats, however eMazzanti Technologies offers a fully-managed detection and response service. In short, this means that we not only detect threats, but we actively review and investigate them. Our expertly-trained researchers and analysts actively look to detect and neutralize threats, resulting in the best possible protection while ensuring company uptime.
At eMazzanti Technologies, we are committed to pairing the right technology with the right people to make sure that threats are detected and responded to in as small a time frame as possible, while guaranteeing the highest regard to accuracy and quality.
Let’s get started
Schedule a meeting to discuss how
eCare SOC can protect your business
Please contact our team or complete the form.
A representative will contact you shortly.
Let's Talk
We’ll chat about your business, how you use technology, and what you want to get out of IT.
Develop a Plan
You’ll choose the IT service agreement that works best for your organization.
Start Your IT Experience
Within days, you’ll be experiencing IT like never before.
T. 844-360-4400
[email protected]
Latest News
Insights to help you do what you do better, faster and more profitably…
View all articles about Cyber Security




